Restricting Directory synchronization to Organization Unit
March 10, 2016 Leave a comment
The default configuration of Azure Active directory connector will take all objects in all domains in the forest to synchronize with Azure Active Directory tenant. In fact, this recommended configuration will facilitate access to the complete Global Address List. With this, the end user using cloud services such as Exchange Online and Skype will have same experience of an on-premises implementation.
In some cases, you may have the requirement of synchronizing only a specific set of users. For instance, the management decision to restrict the cloud service to only users from sales department. In this case you need select users from Sales OU only (assuming the users are in their respective department OUs). In other scenario where you do not want to synchronize the service accounts which are used for only on-premises service.
With filtering you can control which objects should appear in Azure Active Directory from your on-premises directory. Selecting only the required objects for synchronization will provide more security by reducing the surface area attacks. Filtering can also help to limit the number of objects, which can keep the Azure Active Directory Sync database small enough to use the default SQL Express Local Database.
Following are the filtering options which can be applied to the Azure Directory Synchronization tool:
- Domain based: This option allows selection of the domains to synchronize to Azure AD, this will include all object types in the selected Domain(s).
- Organizational Unit based: This option allows selection of the OUs which will synchronize to Azure AD, this will include all object types in the selected in selected OU(s).
- Attribute based: This option allows to filter objects based on attribute values on the objects.
You can use a combination of the above filtering options available. When multiple filtering options are used, the tool will use a logical “and” condition among the filters.
In this post, we will be describing the steps used in configuring the OU based filtering.
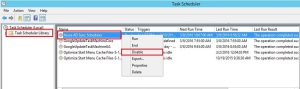
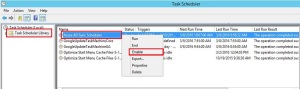
First of all, we will disable the “Azure AD Sync Scheduler” from the local task scheduler. This will eliminate the risk of accidentally synchronizing the objects which we have not yet verified.
Start Task Scheduler from the start menu.
Directly under Task Scheduler Library find the task named Azure AD Sync Scheduler, right-click and select Disable.
Configuring Organizational Unit based filtering
To configure organizational-unit–based filtering, perform the following steps:
Logon to the server that is running Azure AD Connect sync tool using an account that is a member of the ADSyncAdmins security group.
Start Synchronization Service from the start menu.
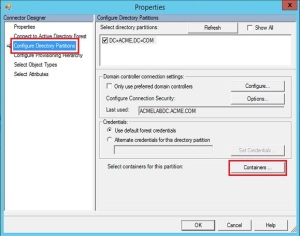
Select Connectors and in the Connectors list, select the Connector with the type Active Directory Domain Services. From Actions select Properties.
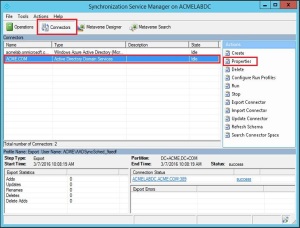
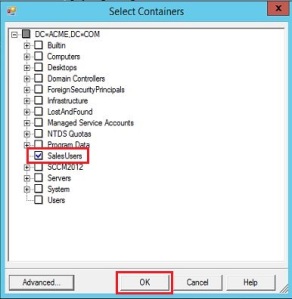
Click Configure Directory Partitions, select the domain you want to configure, and then click Containers.
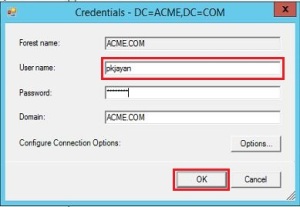
When prompted, provide any credentials with read access to your on-premises Active Directory. It does not have to be the user which is pre-populated in the dialog box.
In the Select Containers dialog box, clear the OUs that you don’t want to synchronize with the cloud directory, When you are done, close the Properties dialog by clicking OK.
Now the filter is applied, do not forget to enable the “Azure AD Sync Scheduler” from the local task scheduler.
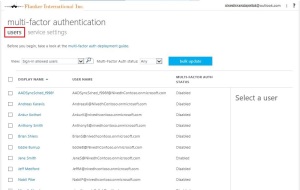
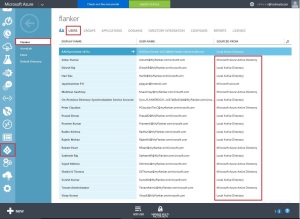
Notice that only the objects under the selected Organization Unit gets synchronized to the Azure tenant.