Enrolling iOS device through Company Portal App
April 29, 2016 Leave a comment
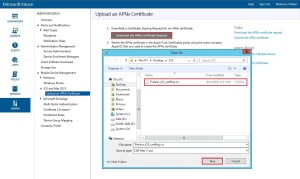
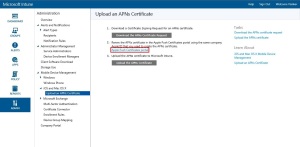
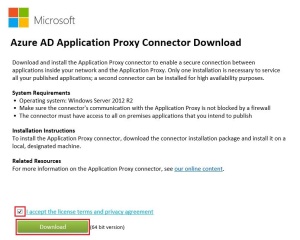
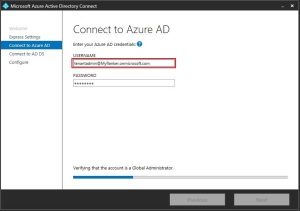
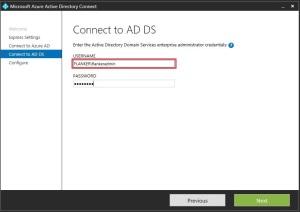
As an alternative to enrollment with the Company Portal app, you can leverage the Apple Device Enrollment Program (DEP) or the Apple Configurator tool to bulk enroll the corporate-owned devices. However, in this post we will be describing the steps required to enroll the iOS devices through Company Portal App.
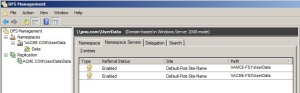
From your apple device (I am using iPhone4 for this demo), launch the App Store application
From the Search field, search for “Company Portal”, you should get the Microsoft Intune Company Portal as first option.
Press the GET button to download and install the Company Portal App
Once the installation is completed, you will see a new icon among your listed apps, Open the Company Portal App to launch it.
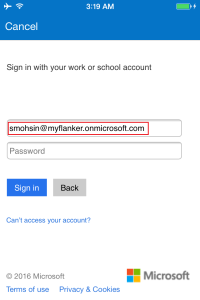
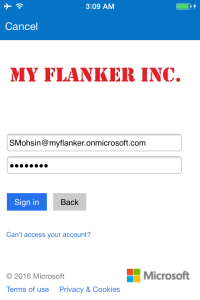
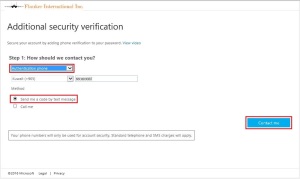
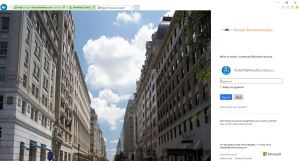
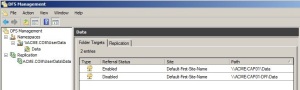
Press the sign In button to login
Key in the domain username, you may notice that the login page will be automatically redirected to your organizations branded login page to enter the username and password.
Notice that the company logo or brand name is displayed
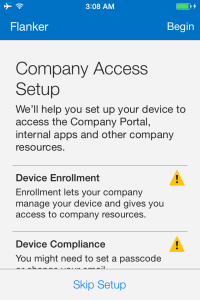
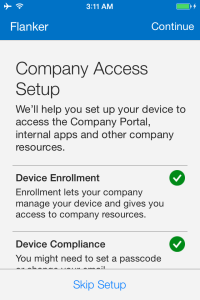
After login is successful, the Company Access Setup wizard will start by displaying the Device enrolment and device compliance status. Press Begin to start the enrolment process.
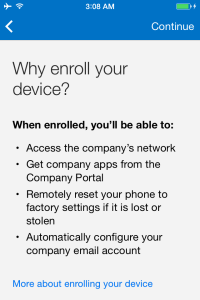
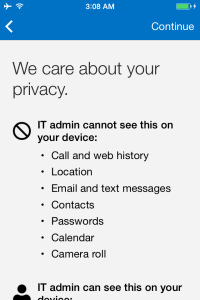
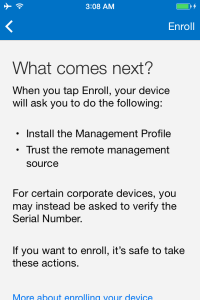
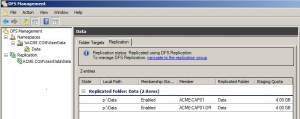
The next couple of screens will show you the benefits and privacy features of enrolling the device.
Press continue twice to run through the information details of enrolling the device .
Press Enroll to initialize the device enrolment process
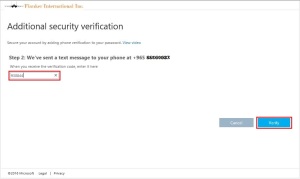
Press sign in to start the device enrolment process
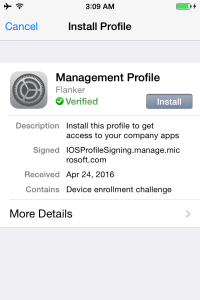
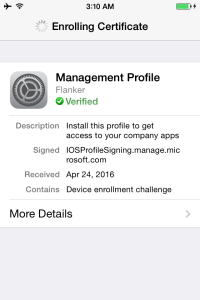
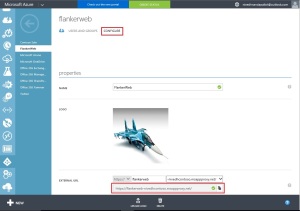
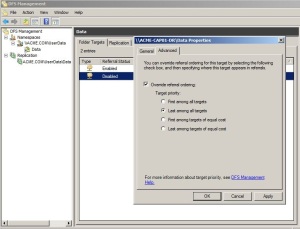
The screen will then jump to the iOS internal management profile installation process. You can see here that the management profile for the domain (flanker) is verified and the same is signed by the Microsoft Intune service IOSProfileSigning.manage.microsoft.com.
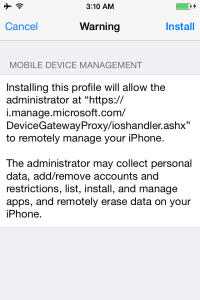
To continue, press the Install button, and confirm when asked to Install Now.
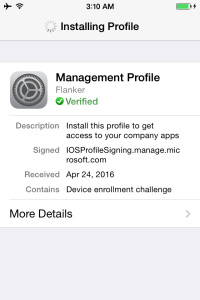
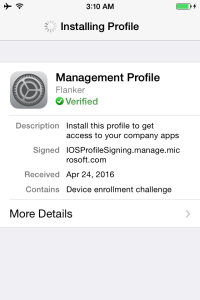
The process will setup all the required management services and certificates
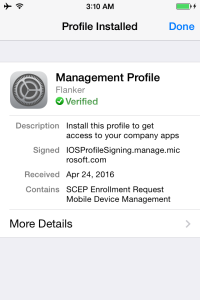
Once again the wizard will ask for one final confirmation. Press Install and Done when complete
Notice that the Company Access Setup displaying the Device enrolment and device compliance status as Successful
press Continue to proceed
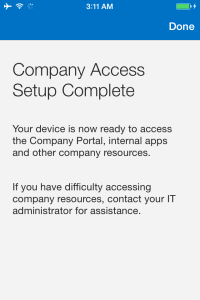
Press Done at the company Access Setup Complete screen
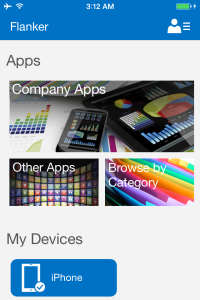
The Company Portal App will display the enrolled device under My Devices. You will now have access to Apps and Device Information
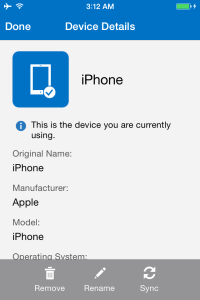
pressing the device will display the details of the device enrolled.
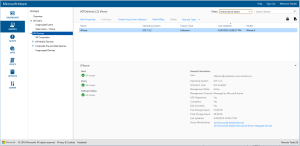
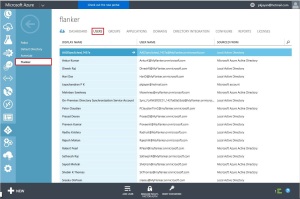
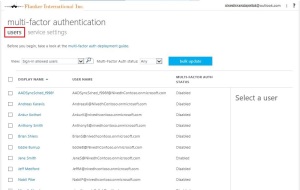
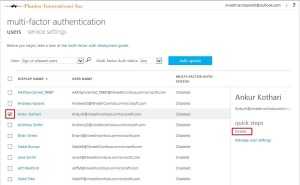
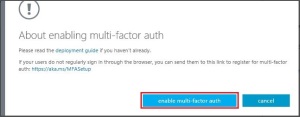
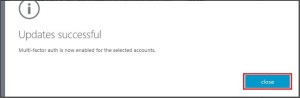
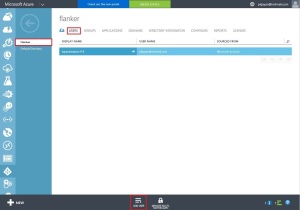
The Intune administrator can view the enrolled device listed in the Intune admin portal as well.